Authentication
As previously mentioned, the Authentication and Authorization solution of the platform is based on Keycloak, which provides centralized authentication and SSO capabilities to all published applications. In the context of the Palatine platform, Keycloak is an essential multi-tenant identity manager that ensures the security and efficient management of users and the tenants they have access to, along with their access roles. In a multi-tenant platform, where various clients or entities share the same infrastructure to manage their connected devices, Keycloak plays a crucial role:
- Centralized Authentication: Keycloak provides a centralized authentication layer, allowing users from different tenants to securely authenticate to the platform once. This simplifies the user experience and avoids the need for repeated authentication when accessing different devices or services.
- Multi-Tenant Identity Management: Keycloak enables the centralized creation and management of user identities, ensuring that each tenant has a separate and secure space to manage their users and devices within the platform. Tenants can define and manage their own sets of users and access policies independently.
- Granular Authorization: With the ability to define roles and authorization policies, Keycloak facilitates the implementation of granular access control. Tenants can assign specific roles to users and devices, ensuring they only have access to resources and data pertinent to their operations.
- Single Sign-On (SSO): Keycloak offers SSO, allowing users to log in once and gain access to devices and services associated with their tenant without needing to authenticate repeatedly.
- API and Device Security: Keycloak provides a robust security layer for Application Programming Interfaces (APIs). It issues and validates access tokens, ensuring that only authorized users and authenticated devices can interact with the platform's resources and services.
- The Keycloak portal also provides capabilities to integrate new applications, allowing the Palatine ecosystem to grow with new applications that would use the same authentication and authorization system as the current environment. This integration ensures that new applications maintain the segregation of information at the Organization/Tenant level.
At the service level, Keycloak provides two interfaces: a public interface through which applications and users authenticate and obtain access tokens, and an administrative interface with independent credentials to prevent any configuration changes that could affect the service.
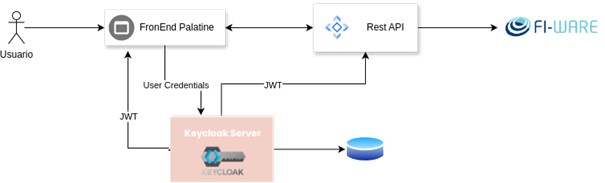
Below is a diagram of Keycloak's authentication scheme in relation to Palatine applications